Let’s be real: most of us don’t think about malware until it’s too late — like when our laptop starts acting possessed, our files disappear, or our bank suddenly thinks we’re shopping in Romania at 3 a.m.
But here’s the thing — malware isn’t just a problem for “hackers” or huge corporations. It’s an everyday threat for anyone using a device connected to the internet (so… everyone). And no, you don’t need to be some super technical wizard to stay protected. You just need to understand what you’re up against — and take some common-sense steps to make your digital life way harder to mess with.
Table of Contents
So, What Is Malware?
Malware is short for malicious software. At its core, malware is any sneaky code designed to mess with your system, steal your data, spy on your activity, or straight-up hold your files for ransom. It’s basically the digital equivalent of someone breaking into your house, digging through your stuff, and then asking you for money to return it.
Types of Malware
Not all malware is the same, and unfortunately, it’s gotten real creative. Here are some usual suspects:
- Viruses – Attach themselves to legit files and spread when opened. Think of them as parasites that make everything sick.
- Trojans – Like the Trojan Horse from Greek mythology: disguised as legit software, but secretly delivers malware once inside.
- Ransomware – Encrypts your files and demands payment to unlock them. It’s like your data getting kidnapped with a Post-it note ransom demand.
- Spyware – Silently watches what you do, logs your keystrokes, and steals your personal info. Creepy.
- Worms – Self-replicate and slither through networks without you doing anything. They’re the worst kind of social butterfly.
- Adware – Blasts you with pop-ups and creepy targeted ads. It also tracks you. Cute.
- Rootkits – Bury themselves deep in your system to avoid detection. Like malware ninjas.
How Malware Actually Gets In
You don’t have to be reckless to get infected — malware is sneaky. Here’s how it usually finds its way in:
1. Phishing Emails
Those email pretending to be your bank or long-lost relative offering you easy money? Yeah — don’t click that. If it’s too good to be true, it probably is.
For more information, check out our previous post on ‘How to Spot Phishing Emails‘.
2. Drive-by Downloads
The term implies that by simply visiting a sketchy website can auto-download malware to your system without you even noticing. Think of it like stepping in gum, you didn’t ask for it, but it’s stuck now.
3. USB Drives and Removable Media
A random flash drive on your desk? Or how about in a parking lot? Could be a trap. Attackers are sneaky, and they prey on people’s curiosity. Don’t plug in stray tech — you’re not rescuing puppies!
4. Outdated Software
Old software has holes in it. Cybercriminals know those holes and slide malware right through.
5. Malicious Apps
That “free flashlight app” from 2012? Probably collecting your contacts, photos, and blood type.
Remember, cybercriminals are sneaky and they’ll often combine multiple of the above mentioned techniques (or maybe others) to increase their chances of successfully infecting systems.
Signs You’ve Got a Malware Problem
Malware likes to stay hidden, but if you pay attention, your device will throw out clues. Here are a few:
- Sluggish performance or random crashes – may indicate malware consuming system resources.
- Strange pop-ups – appearing even when you’re not browsing the internet suggest adware infection.
- Missing or modified files – can be a sign that malware is corrupting your data.
- Unexplained network activity – could mean malware is communicating with remote servers.
- Battery draining faster than your patience – might indicate malware running in the background.
- Disabled Antivirus or security tools – malware often tries to disable antivirus programs and firewalls to avoid detection.
- Unusual behavior – like programs starting automatically, settings changing, or unexplained charges can all point to malware infection.
Best Practices for Prevention
Alright, so how do we fight back? It’s not about paranoia — it’s about layering up your defenses and making life harder for attackers (also called Defense in Depth). Let’s break it down.
1. Keep Your Stuff Updated
Your software gets updates for a reason — most of the time, it’s patching security holes. If you’re still clicking “Remind Me Later,” you’re basically leaving your windows wide open.
- Turn on auto-updates for your OS, browser, and apps
- Pay extra attention to antivirus and security tool updates
- Schedule updates during off-hours if you’re worried about interruptions
2. Safe Browsing Habits
Yes, the internet is full of wonder—and malware. The way you browse the internet significantly impacts your malware risk. Think twice before clicking links, especially in emails, social media messages, or unfamiliar websites.
- Hover over links before clicking. If the link says “paypal.com” but hovers to “paypal123.biz,” hard pass.
- Be cautious with email attachments, even from people you know. If you weren’t expecting a file or the message seems unusual, verify with the sender before opening anything.
- Use an ad blocker. Malicious ads (aka malvertising) are a thing.
- Don’t click “Download Now!” unless it’s from a trusted source.
3. Stick to Trusted Sources
Don’t download sketchy software from even sketchier corners of the web. Trust me, that “free Photoshop” torrent comes with bonus malware.
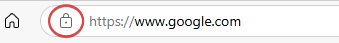
- Use official app stores and verified websites
- Look for HTTPS (the little padlock) before entering sensitive info
- Use strong, unique passwords (bonus points if you’re using a password manager)
4. Use the Right Tools for the Job
Protecting your computer from malware requires a combination of effective security tools. Each tool plays a specific role in creating a strong defense against various types of threats that could harm your system or steal your information.
✅ Antivirus Software
This is your frontline defender. Scans for known threats, blocks bad files, and generally keeps things in check.
- Just keep it updated, or it’s basically a mall cop with no training
- Windows Defender (built-in and solid for most users)
- Bitdefender, Norton, or Kaspersky if you want more control and features
✅ Firewalls
Firewalls monitor traffic in and out of your system. They block shady stuff before it even gets to your computer.
- Windows and macOS have built-in firewalls — make sure they’re on
- A hardware firewall (like from your router) adds another layer of protection
✅ Anti-Malware Tools
Different from antivirus, these look for spyware, adware, and ransomware that traditional antivirus might miss.
- Malwarebytes is a great add-on to your setup
- Run regular scans — even if you think you’re safe
💡 Tip: Schedule automatic or periodic scans. This eliminates human error and forgetting to do it manually.
Steps When Responding to an Infection
Finding malware on your computer can be scary, but taking quick action helps limit damage. The right response steps, tools, and knowing when to call experts can make dealing with malware much easier.
| Action | Quick Summary |
|---|---|
| Unplug from the Internet | Cut off network access to stop the spread immediately. |
| Backup (if you can) | Save critical files—avoid copying the infection. |
| Identify Scope of Infection | Spot symptoms and document what you notice. |
| Use Malware Removal Tools | Run trusted tools to scan and clean your system. |
| Use Boot-Time Scans | Scan during startup to catch hidden or stubborn malware. |
| Call in Reinforcements | Bring in experts if the infection persists or data is at risk. |
1. Unplug from the Internet
If you suspect malware has infected your device, act fast to contain the threat.
Immediately disconnect the infected computer from all network connections – whether wired, wireless, or mobile. This prevents the malware from spreading to other devices or stealing more information.
2. Backup (if you can)
Next, back up important files if possible, but be careful not to back up infected files. Use external storage that you can disconnect afterward.
3. Identify the Scope of Infection
Look for unusual behavior like slow performance, strange pop-ups, or programs starting on their own. Write down when you first noticed problems.
If you’re at work, alert your IT or support team. They’ll need to know what happened ASAP to protect the organization.
4. Use Malware Removal Tools
Several reliable tools can help remove malware from infected systems. Built-in security options like Windows Security (formerly Windows Defender) or macOS’s XProtect provide basic protection and removal capabilities.
Free anti-malware programs like Malwarebytes offer powerful scanning and cleaning features. They can detect threats that regular antivirus might miss.
My top malware removal tools:
- Windows Security/Windows Defender
- Malwarebytes
- Bitdefender Virus Scanner
- Avast Free Antivirus
- Norton Power Eraser
5. Use Boot-Time Scans
Boot-time scanning is particularly effective since it checks for malware before the operating system fully loads. This catches malware that hides during normal operation.
For stubborn infections, try using more than one tool since different scanners might detect different threats.
6. Call in Reinforcements
Sometimes malware problems require expert assistance. If removal tools fail to fix the issue or the infection keeps returning, it’s time to call professionals. Technical staff have specialized training and tools to handle complex infections.
Consider professional help if you notice banking information has been compromised or if personal data appears stolen. These situations might need additional response beyond just removing the malware.
Ransomware infections almost always require professional support. When files are encrypted and attackers demand payment, experts can help determine if recovery is possible without paying.
Organizations should contact their IT security team or hire outside consultants for significant breaches. They can perform forensic analysis to understand how the malware entered and help prevent future attacks.
Final Thoughts
Malware is nasty, sure. But it’s not invincible. With some basic knowledge, solid habits, and the right tools in your corner, you can stay ahead of the game.
And hey — cybersecurity doesn’t have to feel overwhelming or boring. I find it fun (yes, fun) to learn how all this stuff works and help others stay safe while doing it. If this post helped you out, share it with someone who could use a little malware-proofing in their life.
Keep learning, stay curious, and don’t be afraid to ask questions — even the dumb ones. That’s how we all get better.